- Home >> Features >> Technology
A Perfect Guide on What Are Public and Private Keys
- Gayatri
- Friday | 12th March, 2021
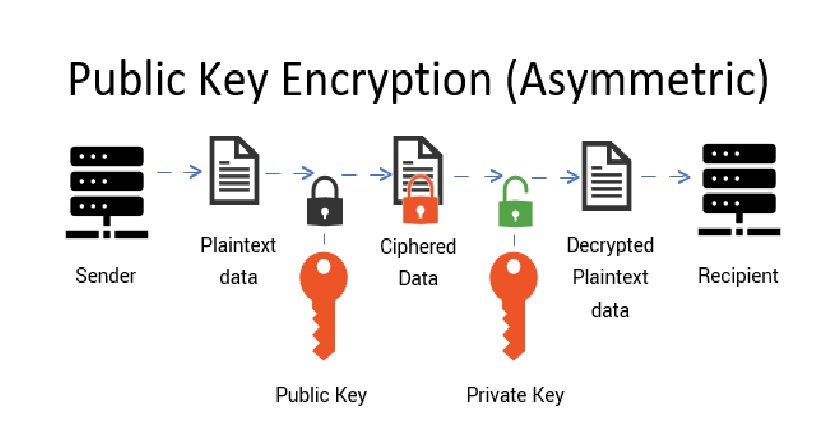
Cryptocurrencies based across blockchain networks depend on public and private keys, which are part of the broader domain of cryptographic defined as either Public Key Cryptography (PKC) or Asymmetric Encryption.
PKC`s aim is to render moving from one condition to another as easy as practicable while causing changing the process virtually difficult, thus showing you have such a key without sharing it. Consequently, the commodity is yet another mathematical operation, which makes it appropriate for checking the validity of anything (such as a transaction) because it could be fabricated. The public and private keys, which are frequently defined by a combination lock (public key) and the actual key to unlock the combination lock, are used in PKC (the private key).
Cryptography Dependent on Shared Keys (PKC)
PKC is based mostly on "Trapdoor Functions" computational primitive, a mathematical problem that is easy to calculate in one path but almost difficult to reverse. To solve this dilemma, computers would require a very long time (hundreds of years) to calculate the correct response. In the form of PKC, mathematical techniques like Prime Computational complexity are stairway mechanisms that render reverse-engineering (i.e., forging) cryptography signatures difficult since they enable the machine to overcome a practically unsolvable maths equation. If you want to do secure trading and need a platform, then you can register through official site .
The Phrases "Public" And "Private" Keys Are Used Interchangeably:
PKC`s key objective is to allow safe, personal communications utilizing encrypted communications in a public channel whereby hostile eavesdroppers could be present. The aim in the sense of cryptocurrency is to show that a spend payment was authorized by the legitimate owner of both the resources and it was not counterfeit, all while taking place on a shared blockchain network amongst peers. What you own when it comes to cryptocurrency is a "private key." Your "secret key" gives the user the freedom to invest in the cryptocurrencies connected with it. It can, like the name implies, stay private since it allows you exposure to your cryptocurrency. A public key resides in comparison to something like a private key, and the public key and the private key are connected cryptographically Just by using the public key, though, it is difficult to identify the private key.
Both A Secret and A Public Key:
Consequently, the public and private keys are equivalent to an email account and a code, however. Alice`s private key, which she already was in one of and acts as the personal key that certain she understands — her secret — will potentially produce hundreds of public keys (addresses) through her private key. When Alice generates a public key address, the address is made freely accessible to all client computers to transfer cryptocurrency, including Bitcoin. Since Alice does have to improve to the publicly accessible email, she is the only person that can read the cryptocurrency sent through the phone number.
What Occurs During A Transaction?
Alice`s public key is her secret key, which she will use to show since she`s the one who made a purchase or received a letter. For e.g., if Alice tries to give Bob a letter over a communication page that Charlie is listened to, she will use her key for encryption and send everything to Bob. Alice also creates a specific value known as a hash production with her post, which is sent to Tim utilizing his public key. Bob will decode and interpret the document using the hashing output, the form, and his private key. Since he only requires Alice`s digital signature or his own secret keys combination, Charlie cannot decode the post. This is where the elegance of stairway functions comes into effect. Since Alice`s message and private key are designed using a hidden door feature, Charlie would be unable to reverse-engineer themselves.
In the UTXO communication channel of Bitcoin, transfers are a sequence of consumers sending or receiving cryptocurrencies to multiple speeches as endpoints. People will submit bitcoins to such an address, recognizing that Alice seems to be the private key holder to such funds if she publishes her public key mostly on the internet. Using simple agreement laws and authentication proofs that now the blockchain pairs are true (Proof of work), miners (people operating the Bitcoin) throughout the Bitcoin blockchain automatically verify and confirm payments in the system to guarantee that nothing of them is fabricated. Consequently, forging transactions in PKC-enabled cryptocurrencies such as Bitcoin is extremely difficult as mathematical proof definitions secure them.

If You Like This Story, Support NYOOOZ
Your support to NYOOOZ will help us to continue create and publish news for and from smaller cities, which also need equal voice as much as citizens living in bigger cities have through mainstream media organizations.











